Have i been pwned?
Содержание:
- They’re Still SHA-1 Hashed, But with Some Junk Removed
- What Is Have I Been Pwned (HIBP)?
- С какой целью создан сайт haveibeenpwned?
- Cloudflare, Privacy and k-Anonymity
- I Haven’t Included Password Length
- Интерфейс сайта Have I Been Pwned
- Keep your passwords unique, and keep them secure
- This is All Still Free (and I Still Like Beer!)
- There’s Now 501,636,842 Pwned Passwords
- Как уменьшить опасность и обезопасить данные от взлома
- Protect Your Accounts Today
- Have I Been Pwned
- Use the 1Password password manager
- Project Svalbard
They’re Still SHA-1 Hashed, But with Some Junk Removed
When I launched V1, I explained why I SHA-1 hashed them:
That’s still 100% true as of today. There are certainly those that don’t agree with this approach; they claim that either the data is easily discoverable enough online anyway or conversely, that SHA-1 is an insufficiently robust algorithm for password storage. They’re right, too — on both points — but that’s not what this is about. The entire point is to ensure that any personal info in the source data is obfuscated such that it requires a concerted effort to remove the protection, but that the data is still usable for its intended purposes. SHA-1 has done that in V1 and I’m still confident enough in the model to use the same approach in V2.
One of the things that did surprise me a little in V1 was the effort some folks went to in order to crack the passwords. I was surprised primarily because the vast majority of those passwords were already available in the clear via the 2 combo lists I mentioned earlier anyway, so why bother? Just download the (easily discoverable) lists! The penny that later dropped was that it presented a challenge — and people like challenges!
One upside from people cracking the passwords for fun was that CynoSure Prime managed to identify a bunch of junk. Due to the integrity of the source data being a bit patchy in places, there were entries such as the following.
- $HEX
- 6dcc978317511fd8
- <div align=\\\’center\\\’ style=\\\’font:bold 11px Verdana; width:310px\\\’><a style=\\\’background-color:#eeeeee;display:block;width:310px;border:solid 2px black; padding:5px\\\’ href=\\\’http://…
Of course, it’s possible people actually used these strings as passwords but applying a bit of Occam’s Razor suggests that it’s simply parsing issues upstream of this data set. In total, CynoSure Prime identified 3,472,226 junk records which I’ve removed in V2. (Incidentally, these are the same guys that found the shortcomings in Ashley Madison’s password storage approach back in 2015 — they do quality work!)
Frankly though, there’s little point in removing a few million junk strings. It reduced the overall data size of V2 by 0.69% and other than the tiny fraction of extra bytes added to the set, it makes no practical difference to how the data is used. On that point and in terms of extraneous records, I want to be really clear about the following:
This list is not perfect — it’s not meant to be perfect — and there will be some junk due to input data quality and some missing passwords because they weren’t in the source data sets. It’s simply meant to be a list of strings that pose an elevated risk if used for passwords and for that purpose, it’s enormously effective.
Whilst the total number of records included in V2 is significant, it also doesn’t tell the whole story and indeed the feedback from V1 was that the 320M passwords needed something more: an indicator of just how bad each one really was.
What Is Have I Been Pwned (HIBP)?
Have I Been Pwned is a popular website that as of 2019 has over 2 million subscribers.
It’s smart to be wary about who you give your details to but this website is designed to help you avoid problems not cause them.
Have I Been Pwned was originally created in 2013 by a security researcher named Troy Hunt. According to Hunt, he created the website in response to the data breach at Adobe Systems which affected 32 million people.
He claims that at the time of the attack, it was easy for hackers to download large batches of stolen account details. But it was very difficult for the average person to find out if their details were included.
When the website launched, it only had the records of five security breaches. Have I Been Pwned now has hundreds of breaches on record and the average person can find out if they are included in seconds.
If you’re still concerned about the intentions of Have I Been Pwned, it’s also worth noting that plans were recently announced to make the entire system open source.
С какой целью создан сайт haveibeenpwned?
Сайт HIBP имеет две основные цели:
- информирование пользователей;
- поддержание и развитие практических навыков работы в области безопасности у создателя проекта.
Ошеломляющее количество взломанных данных включает в себя информацию о миллиардах пользователей, полученную от множества различных веб-сайтов, которые были каким-либо образом скомпрометированы. Достаточно посмотреть краткую статистику и ее масштабы, как минимум, приводят в ужас:
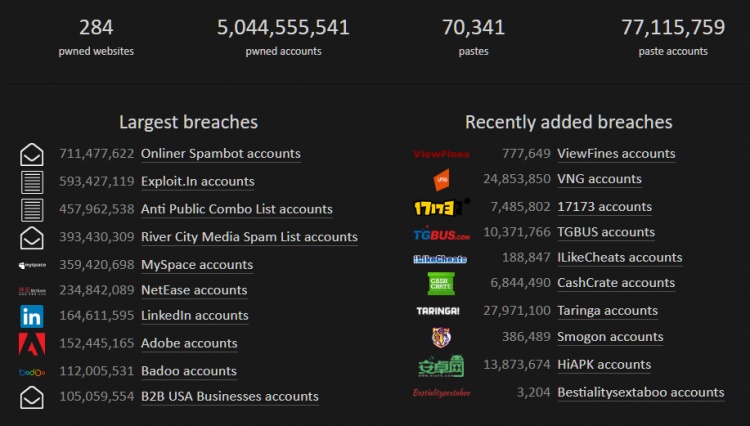
Через руки создателя проекта (Трой Ханта) проходят огромные базы данных персональной информации пользователей. Он не распространяет и не продает эти данные 3-м лицам, напротив — он дает возможность узнать: находитесь ли Вы, среди числа взломанных аккаунтов.
Хант начал работу еще в конце 2013 года. На тот период времени, он анализировал различного рода тенденции возникающие в нарушениях данных, например, как одно из общепринятых — использование одного и того же пароля для разных аккаунтов.
, — сказал Хант. Еще в октябре, 2013 году — компания Adobe была взломана, вследствие чего пострадали 153 миллиона пользователей, их учетные записи (адреса электронной почты, имена, пароли и другая информация) попала в руки к хакерам. Естественно, были и другие компании.
Если кто-то является потенциальной или уже реальной жертвой, при этом не знает об этом — он полностью подвергает себя риску. Хакер имеет возможность воспользоваться скомпрометированной информацией и применить ее в своих корыстных целях: обогащения, унижения, шантажа, уничтожения и другим методам социальной инженерии. Зачастую компании не информируют своих клиентов или пользователей о нарушении данных, до тех пор, пока это не произошло, что, как следствие их защищает и в то же время, делает их еще более уязвимыми для атак.
Если потенциальная жертва будет обладать информацией о нарушении — будет время для того, чтобы принять меры безопасности и защиты личных данных. Нарушения имеют довольно распространенный характер. Многие люди не подозревают какой масштаб и периодичность, с которой они возникают. Данные собранные на haveibeenpwned.com помогут жертвам не только узнать о существующих угрозах, но и позволят задуматься о серьезности рисков возникающих от кибератак в современном мире.
Cloudflare, Privacy and k-Anonymity
In what proved to be very fortuitous timing, Junade Ali from Cloudflare reached out to me last month with an idea. They wanted to build a tool to search through Pwned Passwords V1 but to do so in a way that allowed external parties to use it and maintain anonymity. You see, the problem with my existing implementation was that whilst you could pass just a SHA-1 hash of the password, if it returned a hit and I was to take that and reverse it back to the clear (which I could easily do because I created the hashes in the first place!) I’d know the password. That made the service hard to justify sending real passwords to.
Junade’s idea was different though; he proposed using a mathematical property called k-anonymity and within the scope of Pwned Passwords, it works like this: imagine if you wanted to check whether the password «P@ssw0rd» exists in the data set. (Incidentally, the hackers have worked out people do stuff like this. I know, it sucks. They’re onto us.) The SHA-1 hash of that string is «21BD12DC183F740EE76F27B78EB39C8AD972A757» so what we’re going to do is take just the first 5 characters, in this case that means «21BD1». That gets sent to the Pwned Passwords API and it responds with 475 hash suffixes (that is everything after «21BD1») and a count of how many times the original password has been seen. For example:
- (21BD1) 0018A45C4D1DEF81644B54AB7F969B88D65:1 (password «lauragpe»)
- (21BD1) 00D4F6E8FA6EECAD2A3AA415EEC418D38EC:2 (password «alexguo029»)
- (21BD1) 011053FD0102E94D6AE2F8B83D76FAF94F6:1 (password «BDnd9102»)
- (21BD1) 012A7CA357541F0AC487871FEEC1891C49C:2 (password «melobie»)
- (21BD1) 0136E006E24E7D152139815FB0FC6A50B15:2 (password «quvekyny»)
- …
I added the prefix in brackets beforehand and the source passwords in brackets afterwards simply to illustrate what we’re doing here; they’re all just different strings that hash down to values with the same first 5 characters. In other words, they’re all within the same «range» and you’ll see that term referenced more later on. Using this model, someone searching the data set just gets back the hash suffixes and counts (everything in bold after the first 5 chars) and they can then see if everything after the first 5 chars of their hash matches any of the returned strings. Now keep in mind that as far as I’m concerned, the partial hash I was sent could be any one of 475 different possible values. Or it could be something totally different, I simply don’t know and therein lies the anonymity value.
For the sake of perspective, here are some stats on what this means for the data within Pwned Passwords:
- Every hash prefix from 00000 to FFFFF is populated with data (16^5 combinations)
- The average number of hashes returned is 478
- The smallest is 381 (hash prefixes «E0812» and «E613D»)
- The largest is 584 (hash prefixes «00000» and «4A4E8»)
Junade has written a great piece that’s just gone live on Cloudflare’s blog titled Validating Leaked Passwords with k-Anonymity and he goes into more depth in that piece. As he explains, there are other cryptographic approaches which could also address the desire for anonymity (for example, private set intersections), but not with the ease and level of simplicity Junade proposed. I loved it so much that I offered to build and run it as a service out of HIBP. Junade (and Cloudflare) thought that was a great idea so they offered to point folks over to the HIBP version rather than build out something totally separate. That’s a partnership I’m enormously happy with I appreciate their confidence in my running it.
This model of anonymity is what now sits behind the online search feature. You can see it in action by trying a search for «P@ssw0rd» which will return the screen in the previous image. If we drop down and take a look at the dev tools, here’s the actual request that’s been made:
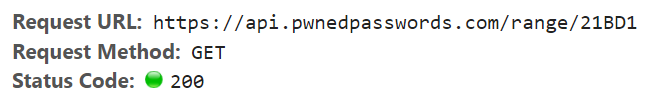
The password has been hashed client side and just the first 5 characters passed to the API (I’ll talk more about the mechanics of that shortly). Here’s what then comes back in the response:
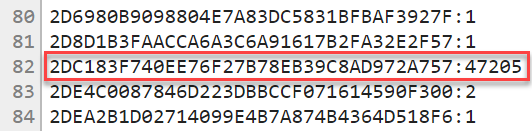
As mentioned earlier, there are 475 hashes beginning with «21BD1», but only 1 which matches the remainder of the hash for «P@ssw0rd» and that record indicates that the password has previously been seen 47,205 times. And that’s it — that’s what I’ve done with Cloudflare’s support and that’s what we’ve done together to protect anonymity and make the service available to everyone. Let me now talk about how you can use the API.
I Haven’t Included Password Length
One request that came up a few times was to include a length attribute on each password hash. This way, those using the data could exclude passwords from the original data set that fall beneath their minimum password length requirements. The thinking there being that it would reduce the data size they’re searching through thus realising some performance (and possibly financial) gains. But there are many reasons why this ultimately didn’t make sense:
The first is that from the perspective of protecting the source data (remember, it contains PII in places), explicitly specifying the length greatly reduces the effort required to crack the passwords. Yes, I know I said earlier that the hashing approach wasn’t meant to be highly resilient, but providing a length would be significantly detrimental to the protection that SHA-1 does provide.
Then, I actually got a bit scientific about it and looked at what minimum length password websites required. In fact, that’s why I wrote the piece on minimum length by the world’s top sites a couple of weeks back; I wanted to put hard numbers on it. 11 of the 15 sites I referred to had a minimum length of 6 chars or less. When I then went and looked at the data set I was using, excluding passwords of less than 6 chars would have only reduced the set by less than 1% Excluding anything under 8 chars would have reduced it by just under 16%. They’re very small numbers.
Then there’s the overhead required to host and search this data, that is the overhead those organisations who use it will incur. It should be very close to nothing with the whole half billion data set. Chuck it in a storage construct like Azure Table Storage and you’re looking at single digit dollars per month with single digit millisecond lookup times. There’s no need for this to be any more complex than that.
So in short, it put the protection of the hashing at greater risk, there was very little value gained and it’s easy to implement this in a way that’s fast and cheap anyway. Some people will disagree, but a lot of thought went into this and I’m confident that the conclusion was the right one.
Интерфейс сайта Have I Been Pwned
После этого откроется главная страница сайта. Сервис «Have I Been Pwned?» работает на английском языке, для большего удобства переведите сайт на русский язык с помощью переводчика в браузере.
Из вкладок меню осуществляется переход на другие страницы сайта. Обычному пользователю будут полезны следующие разделы сайта:
- Во вкладке «Home» происходит проверка почтовых адресов.
- Во вкладке «Notify me» можно зарегистрироваться для получения уведомлений, если аккаунт будет взломан.
- Во вкладке «Domain search» можно получить информацию для поиска по домену.
- Во вкладке «Who’s been pwned» находится подробная информация о ресурсах, которые были подвергнуты взлому в разное время.
- Вкладка «Passwords» служит для проверки паролей.
Keep your passwords unique, and keep them secure
The sad truth, despite all of the above, is that there is no bulletproof method of knowing for sure if one of your passwords has been compromised. While the methods mentioned will keep you as informed as it is possible to be, they cannot be relied upon to be 100% accurate. Why not? The simple answer is that they can only look for credentials that are in the databases they reference. Those databases can only be populated with known, validated, breach records that have found their way onto the dark web or otherwise been shared with the service operators. There will inevitably be a delay between a breach occurring, credentials being stolen, and them ending up in those databases. Assuming, that is, they are not kept out of the public eye by threat actors who may want to exploit them for their immediate gain, or perhaps compile them into a larger database to command a higher value at a later date.
MORE FROMFORBES ADVISOR
How To Protect Your Online Banking Information
ByRebecca Lake
contributor
This means you need to stay on top of your password creation, storage and use game.
The simplest way of doing so is to use a password manager to create random, complex and unique passwords for every site or service. This also ensures your passwords are stored in an encrypted database and, for most people, this will be the easiest way of keeping those credentials secure. Don’t share your master password, the one that unlocks your password manager vault, or individual account passwords for that matter, with anyone. Do make use of two-factor authentication (2FA) wherever it is available, as this provides a second layer of protection just in case someone did get hold of your account password. Without access to the 2FA mechanism, they will still be locked out of logging into your stuff.
This is All Still Free (and I Still Like Beer!)
Nothing gains traction like free things! Keeping HIBP free to search your address (or your entire domain) was the best thing I ever did in terms of making it stick. A few months after I launched the service, I stood up a donations page where you could buy me some beers (or coffee or other things). It only went up after people specifically asked for it («hey awesome service, can I get you a coffee?») and I’ve been really happy with the responses to it. As I say on the page, it’s more the time commitment that really costs me (I’m independent so while I’m building something like Pwned Passwords, I’m not doing something else), but there are also costs that may surprise you:
This is one of those true «Australianisms» courtesy of the fact my up-speed maxes out at about 1.5Mbps (and is then shared across all the things in my house that send data out). Down-speed is about 114 but getting anything up is a nightmare. (And for Aussie friends, no, there’s no NBN available in my area of the Gold Coast yet, but apparently it’s not far off.) And no, this is not a solvable problem by doing everything in the cloud and there are many reasons why that wouldn’t have worked (I’ll blog them at a later date).
If you want to help kick in for these costs and shout me a sympathy coffee or beer(s), it’s still very much appreciated!
There’s Now 501,636,842 Pwned Passwords
Back at the V1 launch, I explained how the original data set was comprised of sources such as the Anti Public and Exploit.in combo lists as well as «a variety of other data sources». In V2, I’ve expanded that to include a bunch of data sources along with 2 major ones:
- The 711 million record Onliner Spambot dump. This was a lot of work to parse varying data formats and if you read the comments on that blog post, you’ll get a sense of how much people wanted this (and why it was problematic).
- The 1.4B clear text credentials from the «dark web». This data resulted in many totally overblown news stories (and contributed to my «dark web» FUD blog post last week), but it did serve as a useful reference for V2. This data also had a bunch of integrity problems which meant the actual number was somewhat less. For example, the exact same username and password pairs appearing with different delimiters:
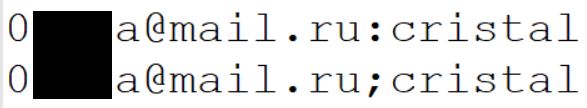
There’s also a heap of other separate sources there where passwords were available in plain text. As with V1, I’m not going to name them here, suffice to say it’s a broad collection from many more breaches than I used in the original version. It’s taken a heap of effort to parse through these but it’s helped build that list up to beyond the half billion mark which is a significant amount of data. From a defensive standpoint, this is good — more data means more ability to block risky passwords.
But I haven’t just added data, I’ve also removed some. Let me explain why and to begin with, let’s do a quick recap on the rationale for hashing them.
Как уменьшить опасность и обезопасить данные от взлома
Пользователь может сделать более безопасным использование своих данных от учетных записей в интернете. Для этого, постарайтесь выполнить следующие требования:
- Не используйте старые пароли от своих учетных записей для новых аккаунтов.
- Не используйте одинаковые логины и пароли при регистрации на разных сайтах.
- Используйте надежные и сложные пароли.
- Для хранения паролей используйте специализированные программы — менеджеры паролей.
- По возможности используйте двухфакторную аутентификацию.
- Если есть возможность, используйте функцию «безопасные платежи», имеющуюся в некоторых антивирусах.
Не рекомендуется использовать снова старые пароли из-за того, что они могли быть ранее скомпрометированы. Новый пароль к учетной записи повысит общую безопасность. Вы, наверное, замечали, что многие сервисы запоминают старый пароль и не разрешают снова его использовать, при проведении изменений в настройках аккаунта пользователя.
Наиболее часто, при регистрациях в интернете, в качестве логина используется адрес электронной почты, потому что он нужен для обратной связи с пользователем. Из-за своей беспечности многие пользователи используют одинаковые пары логин — пароль на разных сайтах.
В этом случае, получив доступ к данным от одного аккаунта, злоумышленник сможет войти в другие учетные записи пользователя. Для большей безопасности имеет смысл пользоваться несколькими электронными почтовыми ящиками: для личных целей, для работы, для регистраций и т. п. Можно создать временную почту для регистраций.
При регистрации на сайтах следует пользоваться надежным паролем. Чем сложнее пароль, тем труднее его подобрать для взлома учетной записи. Онлайн сервисы генераторы паролей или программы менеджеры паролей помогут создать сложный, надежный пароль.
Если создано много разных паролей, их нереально все запомнить. Поэтому для хранения паролей подойдут программы — менеджеры паролей, например, бесплатная программа KeePass, или онлайн сервис LastPass. Для входа в приложение или на сервис хранения паролей, нужно будет создать и запомнить лишь один мастер-пароль, который должен быть надежным.
Вам также может быть интересно:
- Проверка сайта на мошенничество онлайн — 10 способов
- Проверка на вирусы онлайн — 5 сервисов
При двухфакторной аутентификации, для подтверждения входа в аккаунт, помимо ввода логина и пароля, на телефон пользователя придет SMS сообщение с дополнительным кодом, который необходимо ввести для входа в учетную запись или личный кабинет. Если вход совершается с другого устройства, а не с того, которое обычно используется, многие сервисы присылают предупреждения о попытке входа в аккаунт по электронной почте.
При проведении транзакций в интернете воспользуйтесь функцией «Безопасные платежи», которая встроена в некоторые антивирусы. Операция по переводу денег в интернете произойдет в изолированном окне браузера под защитой антивируса. Антивирус заблокирует кейлоггеры и возможность создания снимков экрана, будет следить за буфером обмена.
Protect Your Accounts Today
Data breaches are a frequent occurrence and can happen on any website, regardless of size. If you think that you might have been affected, Have I Been Pwned is the best, and perhaps only, resource for finding out.
Regardless of whether or not your details have already been stolen, the preferred way to protect against data breaches is to never use the same password on multiple accounts. This way, if your details are ever stolen, only one account will be affected.
5 Recent Data Breaches That May Have Put Your Data at Risk
It can be hard to keep up with all the latest online security hacks, so we’ve rounded up some of 2018’s most notable breaches.
Read Next
About The Author
Elliot Nesbo
(26 Articles Published)
Elliot is a freelance tech writer. He primarily writes about fintech and cybersecurity.
More
From Elliot Nesbo
Have I Been Pwned
Веб-сайт Троя Ханта поддерживает базу данных комбинаций имени пользователя и пароля от публичных утечек. Они взяты из баз, которые можно найти на различных сайтах в Интернете или в даркнете. Эта база данных просто упрощает самостоятельную проверку.
Чтобы использовать этот инструмент, перейдите на главную страницу Have I Been Pwned и выполните поиск по имени пользователя или адресу электронной почты. По результатам Вы узнаете, появлялось ли когда-либо Ваше имя пользователя или адрес электронной почты в базе данных. Повторите этот процесс, чтобы проверить несколько адресов электронной почты или имен пользователей. Вы увидите, в каких дампах утечки паролей отображается Ваш адрес электронной почты или имя пользователя, что, в свою очередь, дает Вам информацию о паролях, которые могли быть взломаны.

Если Вы хотите получать уведомление по электронной почте, если Ваш адрес электронной почты или имя пользователя появятся в будущей утечке, нажмите ссылку «Notify me» вверху страницы и введите свой адрес электронной почты.
Вы также можете выполнить поиск пароля, чтобы узнать, появлялся ли он когда-либо в утечке. Перейдите на страницу Pwned Passwords на веб-сайте Have I Beened, введите пароль в поле и нажмите «pwned?» кнопка. Вы увидите, есть ли пароль в одной из этих баз данных. Повторите это столько раз, сколько хотите, чтобы проверить дополнительные пароли.
Предупреждение: Мы настоятельно не рекомендуем вводить пароль на сторонних веб-сайтах, которые запрашивают его. Они могут украсть Ваш пароль. Мы рекомендуем Вам использовать только сайт Have I Been Pwned, который пользуется большим доверием и . Фактически, популярный менеджер паролей 1Password теперь имеет кнопку, которая использует тот же API, что и веб-сайт, поэтому они также будут отправлять хешированные копии Ваших паролей в эту службу. Если Вы хотите проверить, не произошла ли утечка Вашего пароля, Вам следует сделать это с помощью этого сайта.
Если произошла утечка важного пароля, который Вы используете, мы рекомендуем немедленно его изменить. Вам следует использовать менеджер паролей, чтобы можно было легко установить надежные уникальные пароли для каждого важного сайта, который Вы используете
Двухфакторная аутентификация также может помочь защитить Ваши критически важные учетные записи, поскольку она предотвратит вход без дополнительного кода безопасности, даже если они знают пароль.
Use the 1Password password manager
Using a password manager is recommended by numerous security experts as a way of not only storing passwords in a securely encrypted database, but also of generating truly random, complex and unique passwords for every site and service. However, there’s another reason you might want to use 1Password: it will also warn you if any of your passwords have been compromised. The Watchtower feature built into 1Password hooks into the Pwned Passwords search previously mentioned. Rather than having to manually enter every password you use in order to check if it has been stolen or not, Watchtower automates the process in the background. It gets updated whenever a new security breach is reported and added into the Have I Been Pwned database, immediately and automatically alerting you if your password has been found.
Project Svalbard
Five years into Have I Been Pwned, Hunt could feel the burnout coming.
“I could see a point where I would be if I didn’t change something,” he told me. “It really felt like for the sustainability of the project, something had to change.”
He said he went from spending a fraction of his time on the project to well over half. Aside from juggling the day-to-day — collecting, organizing, deduplicating and uploading vast troves of breached data — Hunt was responsible for the entirety of the site’s back-office upkeep — its billing and taxes — on top of his own.
The plan to sell Have I Been Pwned was code-named Project Svalbard, named after the Norwegian seed vault that Hunt likened Have I Been Pwned to, a massive stockpile of “something valuable for the betterment of humanity,” he wrote announcing the sale in June 2019. It would be no easy task.
Hunt said the sale was to secure the future of the service. It was also a decision that would have to secure his own. “They’re not buying Have I Been Pwned, they’re buying me,” said Hunt. “Without me, there’s just no deal.” In his blog post, Hunt spoke of his wish to build out the service and reach a larger audience. But, he told me, it was not about the money.
As its sole custodian, Hunt said that as long as someone kept paying the bills, Have I Been Pwned would live on. “But there was no survivorship model to it,” he admitted. “I’m just one person doing this.”
By selling Have I Been Pwned, the goal was a more sustainable model that took the pressure off him, and, he joked, the site wouldn’t collapse if he got eaten by a shark, an occupational hazard for living in Australia.
But chief above all, the buyer had to be the perfect fit.
Hunt met with dozens of potential buyers, and many in Silicon Valley. He knew what the buyer would look like, but he didn’t yet have a name. Hunt wanted to ensure that whomever bought Have I Been Pwned upheld its reputation.
“Imagine a company that had no respect for personal data and was just going to abuse the crap out of it,” he said. “What does that do for me?” Some potential buyers were driven by profits. Hunt said any profits were “ancillary.” Buyers were only interested in a deal that would tie Hunt to their brand for years, buying the exclusivity to his own recognition and future work — that’s where the value in Have I Been Pwned is.
Hunt was looking for a buyer with whom he knew Have I Been Pwned would be safe if he were no longer involved. “It was always about a multiyear plan to try and transfer the confidence and trust people have in me to some other organizations,” he said.
Hunt testifies to the House Energy Subcommittee on Capitol Hill in Washington, Thursday, Nov. 30, 2017. (AP Photo/Carolyn Kaster)
The vetting process and due diligence was “insane,” said Hunt. “Things just drew out and drew out,” he said. The process went on for months. Hunt spoke candidly about the stress of the year. “I separated from my wife early last year around about the same time as the ,” he said. They later divorced. “You can imagine going through this at the same time as the separation,” he said. “It was enormously stressful.”
Then, almost a year later, Hunt announced the sale was off. Barred from discussing specifics thanks to non-disclosure agreements, Hunt wrote in a blog post that the buyer, whom he was set on signing with, made an unexpected change to their business model that “made the deal infeasible.”
“It came as a surprise to everyone when it didn’t go through,” he told me. It was the end of the road.
Looking back, Hunt maintains it was “the right thing” to walk away. But the process left him back at square one without a buyer and personally down hundreds of thousands in legal fees.
After a bruising year for his future and his personal life, Hunt took time to recoup, clambering for a normal schedule after an exhausting year. Then the coronavirus hit. Australia fared lightly in the pandemic by international standards, lifting its lockdown after a brief quarantine.
Hunt said he will keep running Have I Been Pwned. It wasn’t the outcome he wanted or expected, but Hunt said he has no immediate plans for another sale. For now it’s “business as usual,” he said.
In June alone, Hunt loaded over 102 million records into Have I Been Pwned’s database. Relatively speaking, it was a quiet month.
“We’ve lost control of our data as individuals,” he said. But not even Hunt is immune. At close to 10 billion records, Hunt has been “pwned” more than 20 times, he said.
He laughed. “It still surprises me the places that I turn up.”
Related stories:
- Have I Been Pwned is looking for a new owner
- 1Password nets partnership with ‘Have I Been Pwned’
- After account hacks, Twitch streamers take security into their own hands
- Oracle’s BlueKai tracks you across the web. That data spilled online
- We found a massive spam operation — and sunk its server